The Deceptive World of Social Engineering Social engineering attacks are some of the most effective tricks used...


The Deceptive World of Social Engineering Social engineering attacks are some of the most effective tricks used...

Small businesses in Midtown require reliable IT support to remain competitive and efficient. IT Matters, provides...

An IT support company like IT Matters offers a comprehensive array of services tailored to your businesses in...

As we move deeper into 2024, now is the ideal time to review and optimize your IT budget. A well-planned budget...

As we approach the final quarter of the year, businesses across all industries often face a surge in activity....

As the new school year approaches, students and parents are gearing up for a fresh start. Technology plays a...
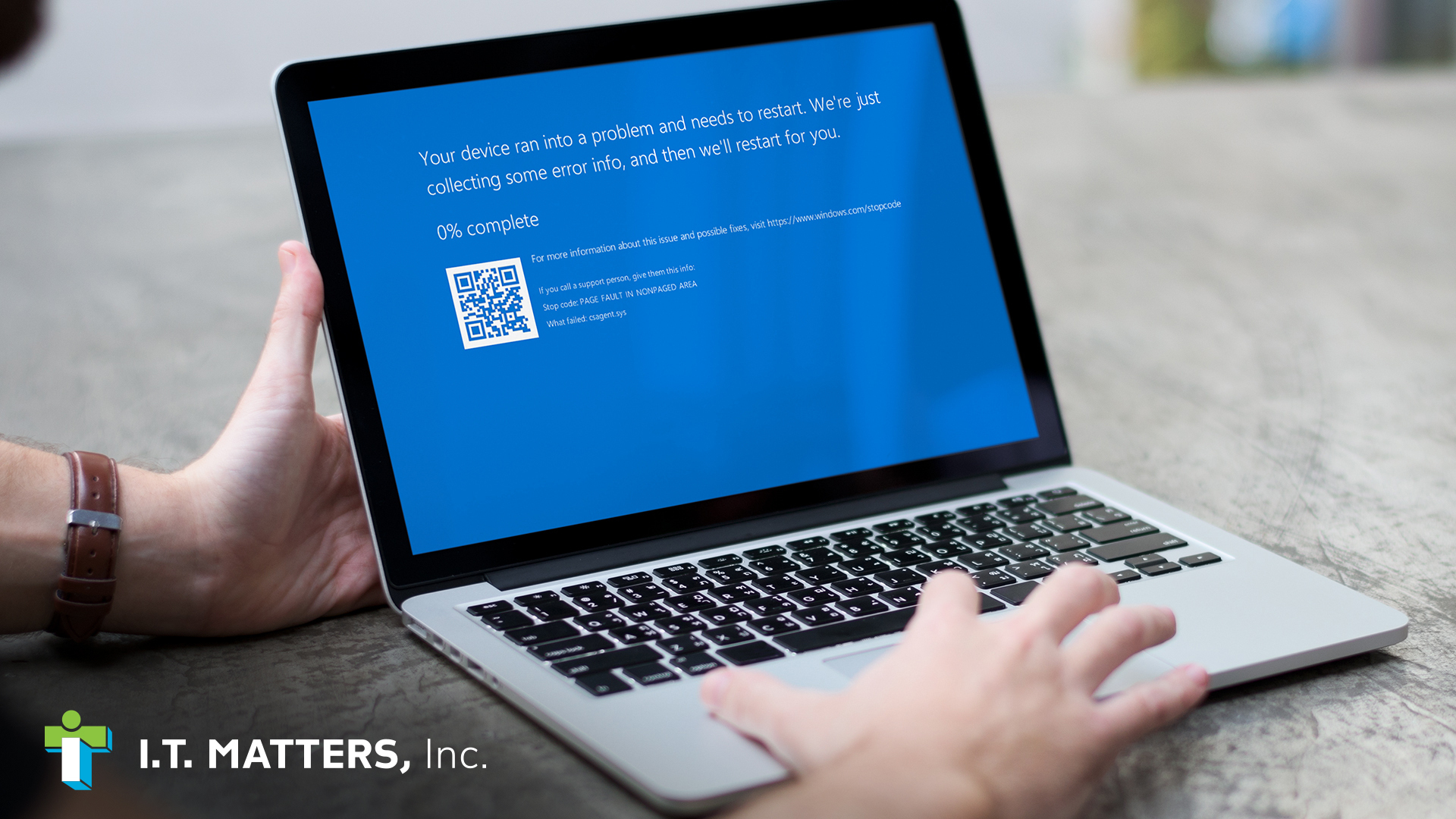
The recent CrowdStrike outage serves as a significant wake-up call for businesses relying on cybersecurity...

A new warning for Google Chrome users has emerged, carrying a critical yet straightforward piece of advice: avoid...

Have you ever considered why your smartphone might benefit from a regular reboot? The Federal Bureau of...

Passwords are our primary defense against cyber threats. Yet, many of us fall into the trap of using generic,...

Email remains a primary communication tool for both personal and professional use, but it also continues to be a...
In an era where online transactions reign supreme, the threat of cyber fraud looms large over businesses and...